Security is one of the biggest concerns facing both individuals and businesses in today’s modern world. Keeping yourself, your data, your devices and your belongings safe when there are threats around every corner is an inescapable challenge, and one that cannot be taken lightly. How can you know which risks pose the greatest threat, and how can you ensure that you, as an individual, are as protected as possible, and are minimising the risks to both yourself and your business?
This is where digital security techniques can be vital assets in protecting yourself in a modern, digital, online age.
What Is Digital Security?
Digital security is all about the steps that you take and solutions that you put in place to protect your personal information, your devices and your assets. While it’s core focus is protecting you as an individual from cyber attacks, following digital security procedures and putting measures in place to protect yourself when operating online can have a big impact on the security of your company as well, since in protecting your own information, devices and systems, you will be less likely to compromise your business’ data and network.
What Is The Difference Between Cyber Security And Digital Security?
While cybersecurity and digital security sound very much like two terms that describe the same idea, and despite people often using them interchangeably, they are two different concepts.
Cyber security is a broad term which encompasses everything that a business can do to protect themselves online. It includes email security, network security, endpoint security, protecting employees, data, policies and processes.
Digital security, on the other hand, is almost a subset of cyber security. It is entirely focussed on the efforts that individuals can take to protect themselves and their own data, devices, finances and assets.
The two terms often get clumped together because they can become closely tied. Companies can enhance their overall cybersecurity efforts by encouraging their employees to follow digital security protocols and techniques, for example, but only using digital security as a means to protect themselves would see them opening themselves to larger scale attacks.
Why Is Digital Security Important?
In this digital age, everything is data driven, and your personal information and assets are critical to your success in business, and in life. But attackers are constantly finding new ways to access that information, whether through phishing emails, malware, deposit fraud and countless other attacks on your person and your online presence. We’ve seen a huge rise over the past few years in social engineering attacks in particular – cyber criminals pretending to be people that you know and trust, and using that trust to get you to divulge personal details, spend your hard-earned money, or give them access to company systems.
Protecting yourself in your online transactions has never been more important, and digital security ensures that you not only have awareness of the threats that you face as an individual, but that you have the tools and knowledge to combat these attacks. Digital security can be the difference between falling for an email that claims to come from your boss asking you to urgently run to the shops and buy iTunes vouchers as end-of-year gifts for the team, and recognising that the address it’s coming from is a fake one. It can be the difference between a hacked Facebook or LinkedIn account, and a protected one.
What Are The Types Of Digital Security That You Can Implement?
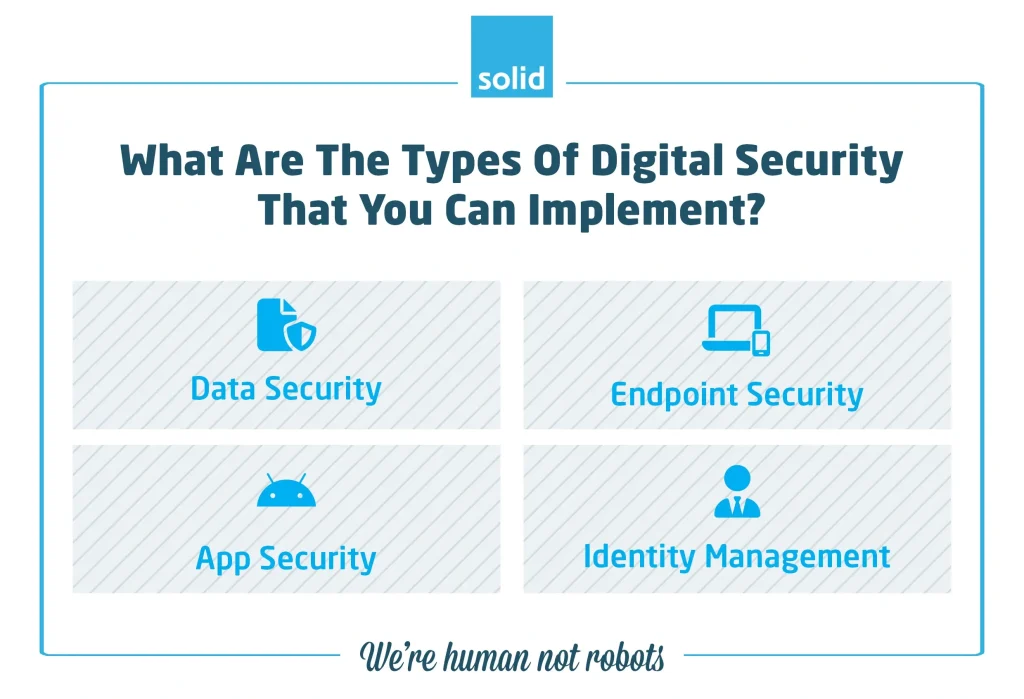
Digital security may be a small section of cybersecurity, but it’s an important one. There are many different types of digital security that you can put in place to protect yourself, such as:
• Data Security
Protecting your personal data is just as important as protecting company information. Personal details like your name, date of birth and contact details can all be valuable assets to cyber criminals who may want to impersonate you in a social engineering attack.
And yet, so often we share these details and so many more with strangers on social media. We don’t think twice about commenting on silly Facebook posts reminiscing about our pets, or sharing maiden names or facts about the year we were born. After all, you may be one of thousands of people who are commenting, and who really cares about your throwaway comments? But these posts are often used to gain access to information that can help an attacker to guess insecure passwords, or answer security questions that you may have set.
• Endpoint Security
Remote and hybrid working have steadily been on the rise over the past few years, and it’s led to another rising trend – that of using personal devices to access company data. And why not – if you have a device that works well, why not use it to log into your company portals. It certainly makes it easier to access the information that you need from wherever you may be in the world, particularly if you’re using a single laptop.
The trouble with using your own laptop to access work information is that you also need to manage its maintenance. And your phone’s updates. And your desktop, and tablet, and second phone… The list goes on. You need to make sure that every device you’re using is secured against threat, which means keeping software up to date, regularly running operating system scans and updates, managing your antivirus software, making sure that your router’s firmware is up to date and so much more.
This is all part of endpoint security, and when you’re working on your own devices, it usually becomes your responsibility to manage your own endpoints, since your company won’t always have the access they need to run the updates and maintenance on your behalf.
• App Security
In the same way that you need to be updating your devices, you also need to make sure that every app that you’re using is up to date as well, and that you’re effectively managing the data that you’re submitting to those apps.
And it’s not just company information that you need to be worried about. Because digital security is all about protecting your personal information, remember? Think about the last app that you installed. What permissions did it want in order for you to use it? Did it ask for access to your contacts, to your photos, to your messages and calls? And did it need all of that access in order to operate?
It’s common for attackers to design seemingly simple and helpful apps which gather far more information than you would want to share in the background. Being careful about which apps you’re installing, carefully reading through their terms and conditions and noting the access that they’re asking for, updating them regularly to ensure that they aren’t vulnerable to attack, and deleting them when you no longer need them, all fall under digital security.
• Identity And Access Management
We work in an age of collaboration and sharing. It’s easier than ever before to work with your team mates, colleagues and friends, even when you’re half a world apart. But it’s important to make sure that only the right people have access to the information that you’re sharing.
It’s all too easy to click a button and get a link to a document that you can share far and wide. It’s far easier, actually, than having to go through your address book and sending each person you want to collaborate with an invite to view the document. But the latter approach is a far safer one to take. Yes, it takes a bit of extra effort to make sure that you are managing the access to documents appropriately, but the benefit of security far outweighs the risk of an open-access link falling into the wrong hands, especially if the document you’re sharing contains personally identifiable information, company data, or even your own intellectual property.
This is just one example of Identity and Access Management – the sharing of documents on a platform. But details like your usernames, passwords, and other login credentials, as well as the websites that those credentials can be used on, all form part of your online identity, which needs to be protected and managed effectively.
What Kind Of Data Is Considered A Digital Security Risk?
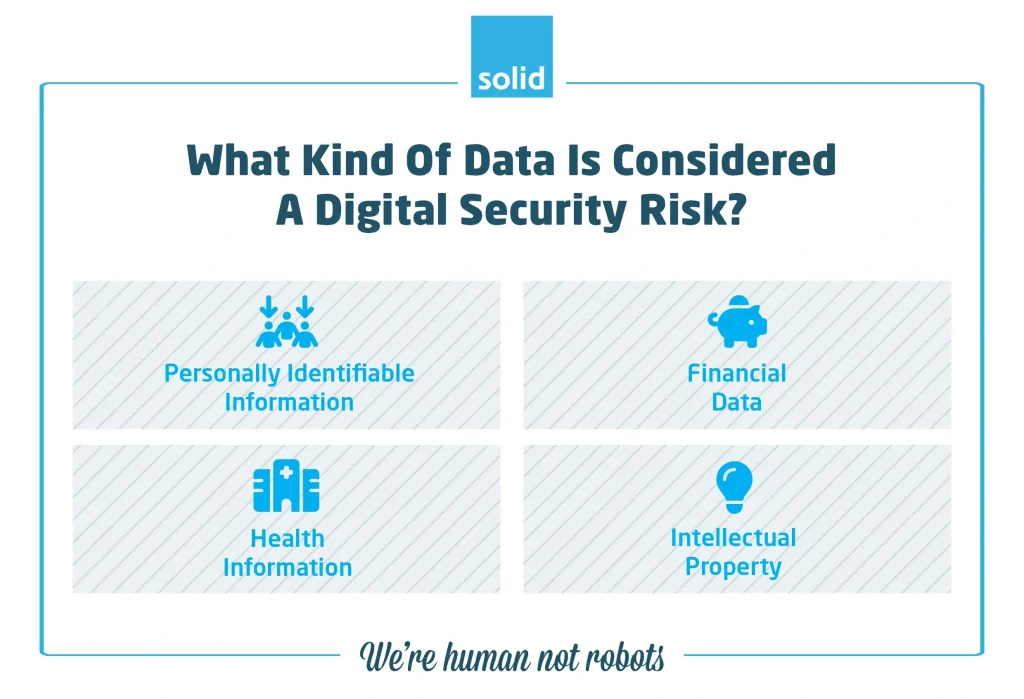
I don’t know if you’ve noticed, but many areas of digital security that I’ve mentioned so far have a lot to do with data. This is because data is a core component of digital identity in today’s world. Which means that digital security plays a large role in protecting that information. But what kind of information can become a digital security risk if it falls into the wrong hands?
• Personally Identifiable Information
Personally Identifiable Information, or PII, is any data that can be used to identify you as an individual. Most people only think of their name, email address, phone number, ID number and login credentials as PII, but even data like your browsing history, location and device details can be personally identifiable, especially if an attacker gains access to the information alongside other PII.
• Financial Data
Banking details, PIN numbers, account balances and transaction histories can all be dangerous information in the wrong hands. Take, for example, an invoice that gets sent to the wrong recipient, or is intercepted before it leaves your outbox. All it takes is for an attacker to change the banking details on the PDF invoice to their own, and send it on to the intended recipient from a fake or spoofed address, and suddenly payments for legitimate services are no longer being directed to you, but to the attacker instead.
• Health Information
Information about your health and wellbeing can seem innocuous, but this kind of personal data can easily be used in a social engineering attack, or leveraged to gain access to further information from your doctor, hospital, or medical aid.
• Intellectual Property
Ideas that you have, unique ways that you operate, plans for the future of your career or your business – all of these are pieces of information that you wouldn’t want to see publicly shared, since it risks others compromising your plans, or taking advantage of your hard work without your being able to benefit from it.
What Are Some Examples Of Digital Security Tools That You Could Use?
There are plenty of digital security tools out there that can aid in your efforts and make it easier for you to protect your online data and presence. Some examples include:
• Multi-Factor Authentication
Daniel has said in the past that he would give someone the password to his account if he had Multi-Factor Authentication (MFA) enabled. They still wouldn’t be able to access his data. That is the level of protection that a second (or third) method of authentication provides. And most social media and email platforms make setting up MFA such a quick and simple process, that there really is no excuse not to enable it.
•Defender For Microsoft
A lot of people think of Defender as an antivirus, but it’s so much more than that. Where antiviruses rely on a store of regularly updated data to check against and identify a piece of malicious software, Defender not only scans your email attachments, but actively prevents you from downloading them or clicking on suspicious links. On top of that, it trains you and your teams to recognise potential attacks, and alerts you to suspicious activity in your Microsoft accounts and platforms.
• Microsoft Intune
Losing a laptop or phone can be frustrating, and even more so when one is stolen from you. Not only do you have to replace a device, but what about all the data that is stored on it. What would happen if that confidential information ended up in the wrong hands? Microsoft Intune is a piece of software that can be installed on any device and wipes critical data from them if a device is lost, stolen, or if the person using it leaves your company.
• Azure Active Directory
Managing login credentials and permissions for teams of people can be a complicated process. But it’s one that Azure Active Directory, also known as Azure AD, makes significantly easier. Not only does Azure AD allow for allocating permissions to groups of people at the same time, making it simple to add a new team member onto your systems and ensure that they the access that they need to succeed, but it also uses advanced artificial intelligence and machine learning to recognise patterns of behaviour and alert you to suspicious activity or potential attacks.
What Other Steps Can You Take To Up Your Digital Security Game?
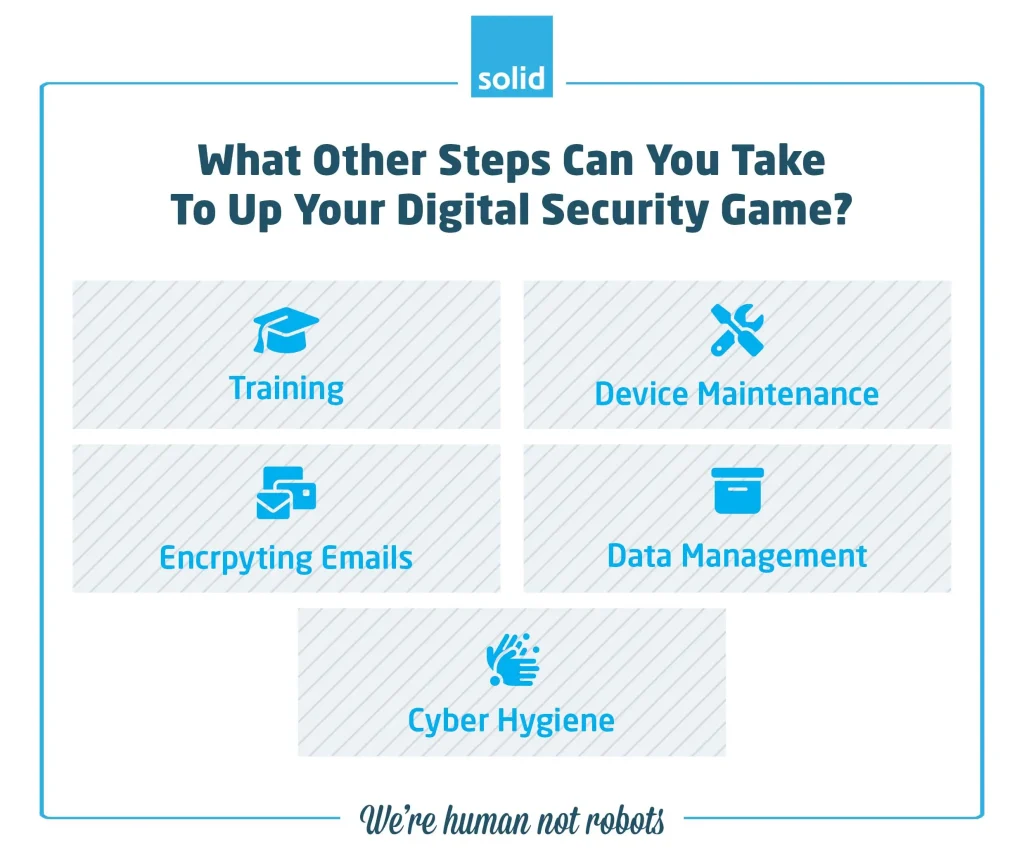
Using the tools available to improve your digital security is a great step in reducing your risk, but it’s not the only step that you could be taking. Putting measures like training, maintenance and cyber hygiene regimes in place will see you making your digital security a priority:
• Training
Because new threats are emerging practically daily, it’s important to keep yourself (and your teams) trained in the latest risks to your data, and the best ways to recognise and avoid them. Regular training sessions will not only boost your own digital security, but will help the humans in your business to do the same, resulting in improved IT security and reduced risk throughout your company.
• Regular Device Maintenance
I know that restarting your computer or your cellphone every time an app needs updating or a security patch comes out can be a pain. It takes you out of your workflow! But installing updates and patches is an important part of keeping your devices secure and your data safe. What you really don’t want is for an attacker to take advantage of a software vulnerability that you could have quickly fixed by turning your machine off and on again. The couple of minutes that it takes to manage updates is well worth it at the end of the day.
• Encrypting Email Communications
Encrypting sensitive information in emails can literally be handled with 3 clicks of your mouse or less. It’s not infallible – encryption can be broken with enough time – but it’s a quick and simple step that adds an extra layer of security, and is especially important when sending confidential details over what is an inherently insecure platform.
• Effective Data Management
Companies and individuals gather so much data in the course of their daily operations. Managing, storing and processing this information effectively isn’t just important for your digital security. When it comes to personal data, protecting it is a legal requirement under acts like POPIA and GDPR if you live in South Africa, the UK or the EU, or if you do business with people who do.
• Practicing Great Cyber Hygiene
While the steps above can be useful on their own, they should also form part of your general cyber hygiene routine. Cyber hygiene, when it comes to digital security, is all about the steps that you can take on a daily, weekly or monthly basis, as an individual to keep yourself and your company protected against attack. We’ve even put together a handy downloadable Personal Cyber Hygiene Checklist so that you can make sure all of your bases are covered.
How Can Solid Systems Help?
Whether you’re looking for data security, endpoint security, a company to manage your apps and make sure that devices are onboarded and maintained effectively, or a partner who can help you with Identity and Access Management, Solid Systems is the technology partner that you need.
For the past two decades, we have been helping both businesses and the individuals who work for them to protect themselves against a wide array of cyberthreats. We have the tools that you need to mitigate the operational risks to your business, and specialise in exceptionally human support that sees your humans working efficiently and effectively, and protecting themselves in their online operations.
If you want to see the difference that working with a technology partner like Solid Systems can make for your business, what are you waiting for? Schedule a free consultation with our Sales team today.
Frequently Asked Questions (FAQs)
Protecting yourself in your online transactions has never been more important, and digital security ensures that you not only have awareness of the threats that you face as an individual, but that you have the tools and knowledge to combat these attacks.
The three most common threats to digital security are data leaks (either through human error, or through social engineering attacks), malicious software (often as a result of phishing attacks) and physical security threats, which can include device theft, but also includes device failures due to natural disasters or wear and tear.