
Risk is a natural part of doing business. There is risk involved in every decision that you make, every client that you sign on, every prospect that you don’t, every email that you send. No matter what industry you may find yourself in, there is risk that needs to be managed, mitigated and delegated. Why would your IT be any different?
This is why you need to perform an IT risk assessment on a regular basis – because with the pace that technology develops, doing it once-off just isn’t enough.
What Is An IT Risk Assessment?
An IT risk assessment is a detailed process that looks at your existing systems, technology, data and processes, determines any underlying vulnerabilities, and ensures that your business is as protected as possible from threats.
Because not all data is equal, when an IT risk assessment is done right, you’ll also find yourself prioritising certain technologies, systems and data over others, ensuring that your time, money and efforts are aligned with your business goals, and that your operations can continue uninterrupted when disaster strikes, all without breaking the bank.
What Are The Benefits Of IT Risk Analysis?
As you can imagine, there are a number of different advantages that can result from assessing your IT risks in a detailed and structured way. These include:
• Understanding Your Risk Profile
If you regularly assess risks to IT security, you will gain a far greater understanding of your overall risk profile. This in turn will allow you to make informed decisions for your business and protect the assets that are critical to your operations.
• Identifying Threats & Vulnerabilities
Because technology never stands still, neither do the threats to it. Between cybersecurity needs, general maintenance, and the potential for natural (and unnatural – I’m looking at you, Eskom) disasters, you need to have a deep understanding of the threats to IT and where vulnerabilities lie in order to effectively protect yourself.
• Mitigating Unplanned Expenditure
Technology is expensive, which is why it’s critical to plan your IT expenditure in advance. Because do you know what’s more expensive than buying a new server? Getting one overnighted to your data centre because your old one fell over unexpectedly and your operations have ground to a halt.
• Managing Data Effectively & Staying Compliant
Managing your data and making sure that it’s stored and processed in compliance with regulations like South Africa’s POPI Act and the EU’s GDPR is a mammoth task and a job all on its own. But IT security risk analysis can help with it. Part of the process involves looking at the data you store, and assigning priorities to it for effective storage, recovery and processing – an activity that can result in far more effective data control.
• Ensuring Uptime
Business continuity is critical to your survival in a market that’s more competitive than ever. Having your operations impacted by threats and vulnerabilities can result in more than just costly replacements and a brief lack of income. It can wreak havoc on your reputation, which will have a far more lasting effect.
8 Steps For Conducting An Effective IT Risk Assessment
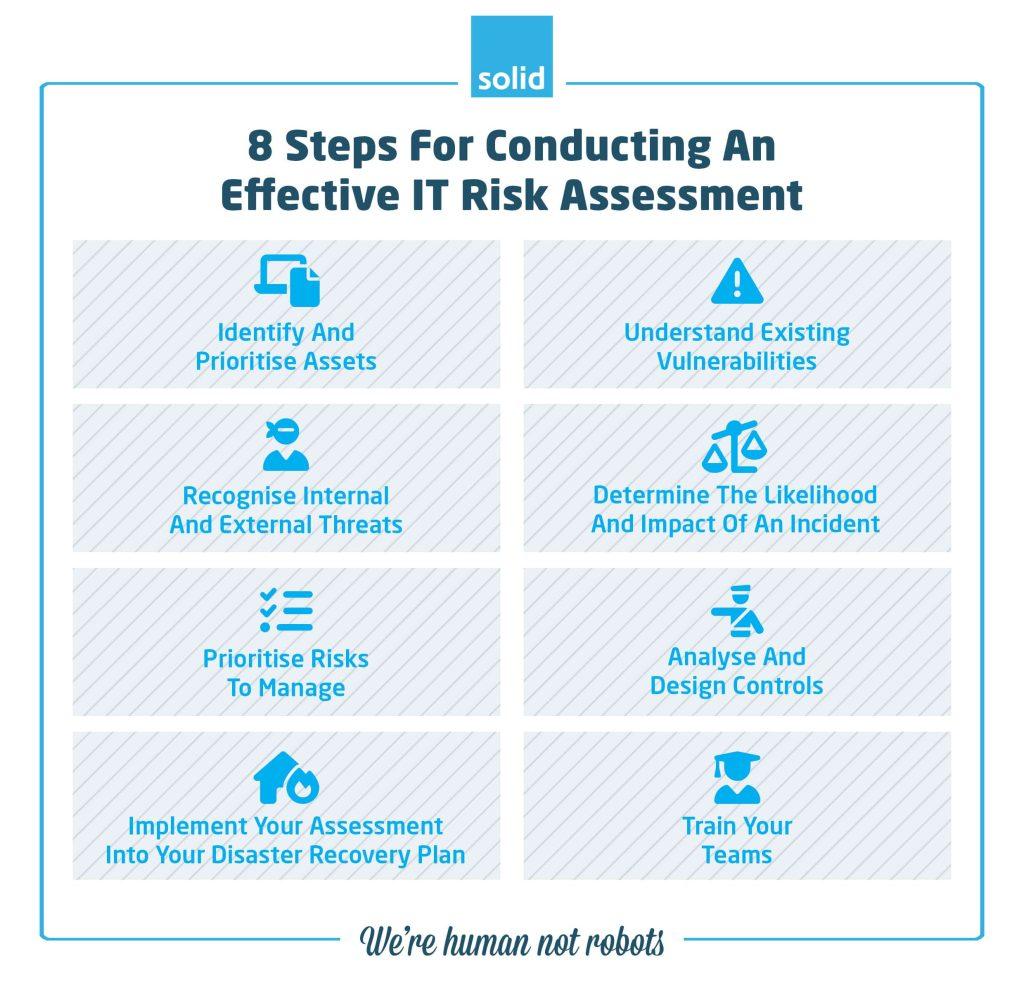
Now that you understand the benefits of conducting regular IT risk assessments the next question is, “What exactly does one involve?” What are the IT risk assessment components need to be taken into consideration?
1. Identify And Prioritise Assets
The first step of your IT system risk assessment should be a thorough systems review. What hardware, software, and data does your company manage, and which teams need access to them? What data is critical to your operations and what is being stored for archive and reference purposes? Understanding what assets need to be managed, and their importance in ensuring business continuity will make the entire IT risk assessment process significantly easier and smoother.
2. Understand Existing Vulnerabilities
Now that you have a better understanding of your systems and processes, it’s time to assess where your vulnerabilities lie. What hardware isn’t operating optimally? Which pieces of software are updated or no longer in use? These factors introduce vulnerabilities into your systems which will need to be addressed, but they are hardly the only vulnerabilities that need to be considered. Your own internal processes, like team members sending confidential information over email, or using wireless networks without a VPN will also factor into IT risks that you will need to address.
3. Recognise Internal And External Threats
With an understanding of potential vulnerabilities, you now need to look at the internal and external threats that have the potential to disrupt your business. In some cases, these will include cyberattackers and hackers. In others they’ll include human error and espionage. And then there are less predictable factors like earthquakes, floods, and load shedding.
While some of these threats will seem less likely than others, it is important to cover all of your bases, and to understand all potential threats to your business. This will make it easier in the later stages of your IT risk analysis to understand which threats need to be addressed as a priority.
4. Determine The Likelihood And Impact Of An Incident
The next step of your IT security risk assessment is gaining an understanding of how likely negative scenarios are, and what the impact for your business would be if one of them occurred. Laying this out in a detailed way will be immeasurably helpful In the next stage of prioritising which risks to address.
5. Prioritise Risks To Manage
You’ve gone through the process of looking at the vulnerabilities and the threats to your business. Now that you have an understanding of these it’s time to prioritise the risks that you are going to be addressing over the coming two years, five years, or more. The more regularly you conduct IT risk assessments the more detailed and thorough your understanding of threats and vulnerabilities will be and the more likely you will be to assign priorities that are achievable over a specific time frame.
One IT risk assessment example which should be handled as a priority is ensuring that all of your software is maintained, patched, and updated on a regular basis. This will significantly reduce the risk of Zero-Day Attacks for your business – a cybersecurity threat which can be costly if not dealt with effectively, and can be easily mitigated by regularly patching your software.
6. Analyse And Design Controls
It’s time to develop processes for dealing with the threats and vulnerabilities that you’ve analysed. This is a critical part of your IT project risk assessment, because it will lead to actions being put in place that can protect your business.
These controls and processes are going to be impacted by the priorities that you have set out in previous steps, since you are going to want to ensure that these are dealt with as quickly and as effectively as possible. But that does not mean that you will only be addressing the highest priority risks. Just because a risk is critical to your business continuity does not mean that it is the only risk that needs to be addressed. During this process you will also be looking at easy wins. For example, there may be small steps that you can take to increase your security without requiring significant budget or time to implement, which may not align with a specific priority, but which will protect your business overall.
7. Implement Your Risk Assessment Into Your Disaster Recovery Plan
What makes an IT risk assessment procedure truly meaningful and impactful in a business is when the theoretical risks that have been analysed and assessed, and the processes that are developed for dealing with them, are put into action. The best way of doing this is to incorporate your IT risk assessment and the controls that you have designed for managing risk into an incident response plan or Disaster Recovery Plan.
This will make it significantly easier for stakeholders across your company, whether in your IT team, management, your CEO, or even your investors, to understand the actions that you are taking to mitigate risk and their roles in making sure that these actions take effect when an incident comes to light.
8. Train Your Teams
Once your IT risk assessment is complete and has been included in your disaster recovery plan, you will need to make sure that all of your team members understand their roles in making sure that incidents do not take place because of human error, and what their roles are in dealing with external disasters when they do occur.
Ensuring that your teams understand the threats to your business, and the risks that you face in your operations on a daily basis, will see them connecting to your company and being in a better position to protect your business.
Where Does Solid Systems Come In?
One of the first steps that we take when working with a new company is to perform a systems review. This forms part of our Managed IT Services, and is just one of the ways that we protect the businesses that work with us. It gives us a good understanding of your systems, your hardware, your processes, and your users, and provides us with the perfect opportunity to perform a thorough IT risk assessment as a priority.
Why do we do this? As an IT company that has been operating for over two decades we have vast experience in helping businesses to understand the risks that they face when it comes to IT implementation and to ensure that those risks are addressed in a strategic manner. This is just one of the ways that we set ourselves apart as one of the best IT companies in South Africa.
Want to see for yourself what an IT risk assessment involves and how Solid Systems can make a difference for your business? Get in touch with us today.
Frequently Asked Questions (FAQs)
Conducting an IT risk assessment is a detailed and thorough process which ensures that your systems, technology and data are as protected as possible from threats. There are 8 steps involved in an effective IT risk assessment:
1. Identify and prioritise assets
2. Understand existing vulnerabilities
3. Recognise internal and external threats
4. Determine the likelihood and impact of an incident
5. Prioritise risks to manage
6. Analyse and design controls
7. Implement your risk assessment into your disaster recovery plan
8. Train your teams
An IT risk assessment is a detailed process that looks at your existing systems, technology, data and processes, determines any underlying vulnerabilities, and ensures that your business is as protected as possible from threats.
Because not all data is equal, when an IT risk assessment is done right, you’ll also find yourself prioritising certain technologies, systems and data over others, ensuring that your time, money and efforts are aligned with your business goals, and that your operations can continue uninterrupted when disaster strikes, all without breaking the bank.
When conducting an IT risk assessment, there are a number of different components that need to be looked at. These include your existing systems, the technologies that you plan to implement in future, the various types of data that your company manages, and the processes that you have in place. Analysing each of these components for vulnerabilities, and understanding the range of threats that face your business, both internally and externally, all form part of conducting an effective IT risk assessment.
Risk is a natural part of doing business. There is risk involved in every decision that you make, every client that you sign on, every prospect that you don’t, every email that you send. No matter what industry you may find yourself in, there is risk that needs to be managed, mitigated and delegated. Why would your IT be any different? This is why you need to perform an IT risk assessment on a regular basis – because with the pace that technology develops, doing it once-off just isn’t enough.
Because technology never stands still, neither do the threats to it. Between cybersecurity needs, general maintenance, and the potential for natural (and unnatural – I’m looking at you, Eskom) disasters, you need to have a deep understanding of the threats to IT and where vulnerabilities lie in order to effectively protect yourself. An IT risk assessment allows you the time to do just that and ensure that your business is taking every possible step to keep your company secure.
As you can imagine, there are a number of different advantages that can result from assessing your IT risks in a detailed and structured way. These include:
– Understanding your risk profile
– Identifying threats and vulnerabilities
– Mitigating unplanned expenditure
– Managing data effectively and staying compliant
– Ensuring uptime
IT risk assessments should be run on a regular basis – at least once per year. Because the threats to your business and the vulnerabilities within your systems and data are constantly evolving, you need to ensure that your risks are being mitigated or delegated, and that your company is as protected as possible.





