There are almost countless threats facing businesses that operate in today’s modern, digital world. You have to worry about data security, about email security, about cyber security in general, and have to manage so many different risks that it can be hard to keep track of which one poses the most threat. Because not all risks are equal. Some can cause more damage than others. And Spyware is one of the most dangerous threats to face any business in any industry.
What Is Spyware?
Even though it has been around almost as long as the internet has, I’m always surprised by how many businesses don’t know the meaning of Spyware, or how dangerous it can be. Even worse, they don’t realise how much of a threat Spyware poses to their business.
So what is Spyware in computer terminology? You can think of Spyware as a virus which does what the label suggests – spies on your digital activity. It’s an overarching term for a wide range of different threats and viruses all aimed at collecting information without your knowledge, and using it to either extort money from you, your vendors and your clients, or to disrupt your operations. It’s a type of malware, or malicious software, which is designed to go undetected for extended periods of time, allowing it to cause as much damage as possible.
How Does Spyware Work?
While a definition of Spyware can be helpful in understanding the term, what most businesses really want to know is what can Spyware do exactly?
Because there are so many different types of Spyware which each function in different ways, it’s hard to provide more than a high level answer of what is Spyware and what does it do. Each different type of Spyware will act in different ways according to the attacker’s needs. But one area which is consistent is that Spyware operates in secret. Most Spyware is designed to go undetected. The goal is for attackers to gather as much information as they can without being noticed. A lot of the time, the first time a company will learn that they’ve been targeted by Spyware is when an attacker makes their final move – holding business data ransom, sabotaging emails that you have sent to clients and vendors, hacking your bank account or website, or publishing confidential information online for other attackers or competitors to use.
It is because Spyware is designed to go undetected that it is so dangerous. The longer an attacker is able to infiltrate your systems without your knowledge, the worse the attack itself will be when it eventually takes place.
What Are The Different Types Of Spyware That Attackers Use?
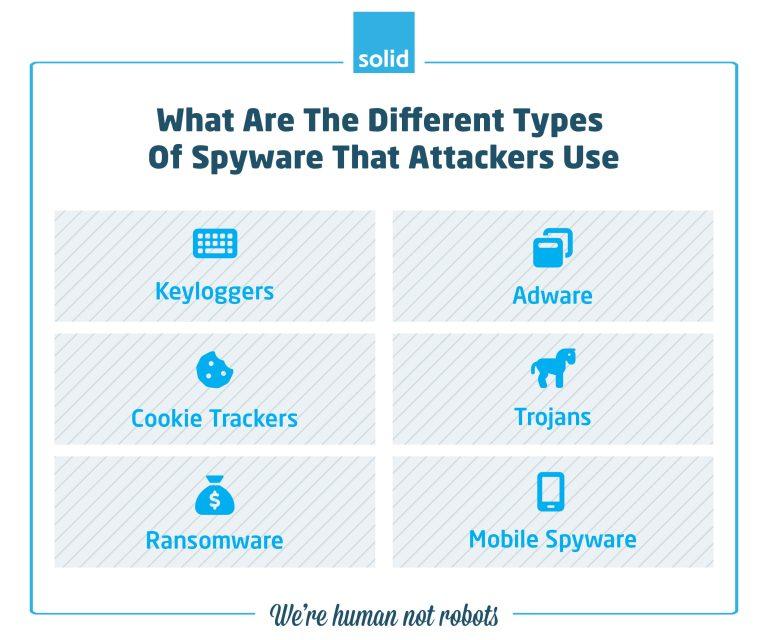
I mentioned before that Spyware is a type of malware. And while not all malware is Spyware, there are plenty of different types of malware that fall into the Spyware category, allowing attackers to gain monitor user activity in a variety of different ways.
1. Keyloggers
Keylogging Spyware allows an attacker to track user credentials like usernames, passwords and answers to security questions, or even credit card details, by keeping logs of the keys and patterns that a person presses on their keyboard.
2. Adware
You’ve likely seen those pop-up windows that open when you visit a website. This is known as adware, and some of them are perfectly legitimate advertising for real businesses. But adware can also be used by attackers to redirect you to malicious websites, or get you to download apps and resources which seem like they would be useful, but in reality are providing attackers with access to your system.
3. Cookie Trackers and Tracking Cookies
You’d be surprised by how much information can be gathered through cookies. This isn’t to say that all cookies are bad. Chocolate chip ones in particular are delicious! I kid, of course. There are useful cookies that make browsing websites that you visit often far easier, or personalise your experience. But when attackers use cookies without you consenting, or even being aware of your information being gathered, they can use details about the sites you visit, your location, and your personal information to orchestrate an attack or target you with phishing mails and malicious links.
4. Trojans
If you’ve heard the story of the Trojan Horse, then you likely have an idea of what Trojan Spyware does. It acts as a legitimate piece of software which you might find useful, but once the software has been installed, it makes use of other Spyware techniques like keylogging and tracking cookies to gather data about your business, or otherwise disrupt your operations. The key feature here is that the software will seem useful in and of itself, and often be offered free of charge. If something seems too good to be true, such as a website offering free versions of Microsoft apps, for example, it’s a good idea to be wary.
5. Ransomware
While data gained by most Spyware can be used in a variety of different methods, from intercepting communications and performing social engineering attacks, to orchestrating deposit fraud for example, Ransomware has a very particular goal in mind. That is to gain access to as much data as possible, encrypt it so that it cannot be accessed, and hold it ransom while your operations grind to a halt.
Many businesses have no choice but to pay the extortionate ransom demands, as without backups of their data, their businesses would crumble if the information is deleted or becomes irretrievable. And what’s worse is that, once ransom demands have been received, there is no guarantee that the attacker will revoke their access, or that they won’t leave a backdoor for a further attack later down the line.
6. Mobile Spyware
While most Spyware targets desktop machines and laptops, there are plenty of reasons why an attacker may want to target a smartphone or tablet as well. Mobile Spyware provides attackers with access to more personal data than any other devices, thanks to the photos and videos that users take of themselves, their homes, their pets and loved ones. Then there are the texts, the WhatsApp messages, the voice notes and the phone calls that you make, which an attacker can be privy to if they have managed to get Spyware onto your mobile. And because people want to be connected to their work no matter where they may be, phones often also have access to email addresses and company documents.
What Are The Risks And Effects Of A Spyware Attack?

We’ve answered the question of what is Spyware and how does it work. But, like many other business owners, managers and employees, you may be thinking to yourself: “But why would an attacker target me?” This is especially the case, I’ve found, with owners and employees of small and medium enterprises. There is this idea that only large companies are at risk of being attacked. You consider yourself as small fry next to the payout that an attacker could gain from infiltrating a multi-national conglomerate.
But in reality, smaller businesses are actually far easier to target. And it’s largely because they don’t think of themselves as being vulnerable. This means that they don’t implement stringent security measures, which in turn makes it easier for attackers to gain access to their systems. They don’t have backups in place, which makes them a better target for ransomware attacks, since they are more likely to pay the ransom to retrieve their data.
With this in mind, let’s look at what a spyware attack looks like go through some of the effects that a successful Spyware attack can have on a small business:
1. Identity Theft
Spyware provides attackers with almost unlimited access to your online activities. Keylogging Spyware means that they can see the usernames and passwords you type in, which can then provide them with access to company documents, to your email address, even to your credit card details. All of this gives an attacker the perfect opportunity to steal your identity. They can send emails as you to vendors and clients, changing banking details for payment to their own, reading, copying and altering company files, or making purchases using your credentials and having them shipped to themselves.
2. Unauthorised Access
As a business, you try your best to ensure that your humans have access to the tools and data that they need to work effectively and efficiently. You carefully organise team members into groups to ensure that they have the right data permissions. You painstakingly label sensitive information, and ensure that it gets encrypted so that it’s more difficult to compromise. And then one of your humans falls victim to a Spyware attack. All of that hard work is moot, because you’ve got an attacker who is able to infiltrate your systems without your even being aware. What they do with the information they find can vary – they could hold it ransom, they could leak it online, they could use their existing access to gain further access from other employees. But no matter what their endgame might be, having someone gain unauthorised and unfiltered access to your company data can never end well.
3. Deposit Fraud
We’ve been seeing a lot of this over the past couple of years. Once an attacker has access to your email credentials, it is easy for them to monitor incoming and outgoing communication. As soon as you send out an invoice from a compromised mailbox, they can intercept that mail and adjust the attached document to reflect their own banking details instead of yours. Your clients and vendors will receive the invoices that they are expecting, and it will all look legitimate. It may even come with an email that you have written. The only difference will be the bank that payment needs to be made into. And if the vendor or client hasn’t worked with you before, they won’t even question it. Even vendors who have worked with you before may notice the change and effect it without question – people change banks all the time, don’t they?
4. Data Leaks
While holding your company’s data ransom is certainly one route that Spyware attackers may take, there is another trend that is on the rise. Since regulations like Europe’s GDPR and South Africa’s POPI Act have come into effect, attackers are taking full advantage of the chaos they can cause, and are leaking information online. This data can include personal information about your clients, their credit card details, usernames, passwords and more.
Why would attackers do this? First of all, there are plenty of attackers out there who are purely in it for the disruption that they can cause to businesses. They want to see the world burn, so to speak. And data leaks can have detrimental impacts on companies, from incurring fines, to destroying their reputation.
Another reason is that attackers often form communities. They help each other to compromise businesses, and sharing personal data far and wide means that more cyber criminals have access to it and can use it for their own advantage.
How Can You Prevent Spyware Attacks?
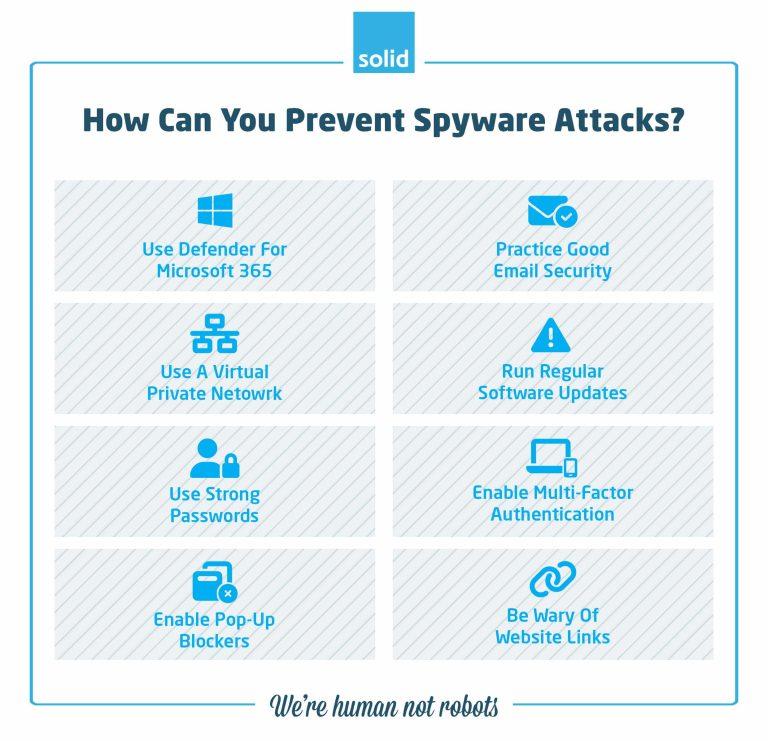
As you can tell, Spyware poses a danger to businesses both large and small, and should be prevented at all costs. But what is anti-Spyware software that you can use, and what steps can you take to ensure that you, your business, and your humans are all safe from Spyware attacks?
1. Use Defender For Microsoft 365
Defender for Microsoft 365 is the next evolution of an anti-virus. It doesn’t just scan mails and downloads for viruses, but helps you to prevent them from being downloaded at all. It adds a layer of protection when clicking on email links, and allows you as a business to train your employees in the latest best practices when it comes to email security. It can also help you to detect unauthorised access or unusual activity on platforms like OneDrive and SharePoint, making it easier for you to detect attacks, and stop them in their tracks.
2. Practice Good Email Security
Even if you have Defender for Microsoft 365 in place, it is still a good idea to research and implement best practices when it comes to email security. There are the ones that you will have heard over and over again – don’t click on suspicious links, don’t download attachments that are sent from strange addresses. But there are also best practices that fewer people know about. For example, always check the sender of an email, and be on the lookout for spelling errors in addresses and domain names. It is easy for an attacker to claim to be someone you know, even if they don’t have access to the correct address for that person.
3. Use A VPN
This is especially important if you’re going to be using public wireless networks. It’s great to be able to access your mails while you’re in line at the local coffee shop. But if you’re not protected by a Virtual Private Network (or VPN), it is all too easy for an attacker to perform a man-in-the-middle attack and intercept the data that you’re transferring over the network. Even more sneaky, attackers have been known to create their own ‘free WiFi’ networks, which transfer all data directly to them without them needing to lift a finger. This is one of the biggest threats in network security. Using a VPN means that the data your send over a wireless network is encrypted, making it difficult to intercept or interpret, and making it less likely that an attacker will be able to trick you into downloading spyware onto your device.
4. Run Regular Software Updates
Everyone hates software updates. They slow down your day and often mean having to sit around twiddling your thumbs while you wait for them to be completed. But don’t let that stop you from installing updates as soon as they are available. Updates and patches are usually released for good reason. They address security vulnerabilities that may have been discovered, and ensure that your devices are as protected as possible at all times.
5. Use Strong Passwords
Using strong passwords, and using different passwords for every platform, will make it a lot more difficult for an attacker to gain access to your accounts. Even with Spyware which can monitor your keystrokes, if you are using different passwords for different sites and apps, an attacker gaining access to one platform will not necessarily see your company data becoming compromised.
Better still, use a password manager to keep track of user credentials across different sites. This will mean that you will not need to type in your password for each of the sites and apps that you access, which will further restrict the access that an attacker can gain, even if they are using keylogging software.
6. Enable Multi-Factor Authentication
On top of having a strong password for each platform, I cannot recommend MFA or two factor authentication strongly enough. If you have multi-factor authentication (MFA) enabled on your accounts, even if an attacker does gain access to all of your passwords, they still won’t be able to login without direct access to your cellphone or, if you go the biometric route, your fingerprint. MFA is so easy to set up and adds such a strong layer of protection against attack, that it really is a must for any business who takes their security seriously.
7. Enable Pop-Up Blockers
This piece of advice is both a security measure, and a bit of a lifestyle hack. Is there anyone who actually enjoys pop-up ads? Adding a pop-up blocker to your browser will not only make for a much more pleasant browsing experience, but will also add a layer of protection for your humans. If they aren’t seeing the pop-up ads that attackers are displaying, there will be less chance of them accidentally clicking on one and being taken to a malicious website where Spyware can automatically be installed.
8. Be Wary Of Website Links
You may be wondering why I’ve mentioned this again, when I already said that you need to practice good email security. But the fact is that it’s not just email links that you need to be wary of. Well meaning family and friends often forward links to giveaways that sound too good to be true, or to fun and amusing pictures that they’ve come across, or to petitions that their friends have passed along. But you need to be wary of these links as well, even if they are coming from someone you know. Your mom might not know any better than to enter that giveaway for a free iPad, but you do. I’ve said it before in the article, and I’ll say it again. If something seems to good to be true, it probably isn’t legit.
How Do I Remove Spyware From My Device?
Now you know how to prevent Spyware attacks, but what if your devices are already infected? Because Spyware is designed to go undetected, it can be difficult to tell if you have Spyware installed on your devices. There are a couple of signs that you can look out for – Spyware has a tendency to slow machines down, since it is constantly transferring data to an attacker. And while your anti-virus should pick up on Spyware installations, if it’s out of date, or if the Spyware is new and anti-viruses have not picked up on it yet, there is a chance that it can pass by undetected.
If you suspect that your system might be compromised, there are a couple of steps that you can take:
1. Let Your IT Team Know
The chances are that if you’re reading this section, you aren’t too familiar with the ins and outs of technology. We don’t blame you – not everyone is a tech pro. Which is why the first step that you should take if you suspect that your system is infected is to inform your Technical Team. Whether that’s an internal IT team, or a company like Solid Systems who is looking after your technology, letting them know will help them to contain the damage that could be caused by Spyware. They can review your email history to check if any suspicious mails have been sent, can run scans to detect any unauthorised activity, and can ensure that your machine is safe to use.
2. Reset Your Passwords
This is step number 2 for a reason. Before you go ahead with resetting your passwords, you need to make sure that the Spyware has been removed from your devices. Otherwise, all of those new passwords are going to be passed straight on to the attacker all over again. So, once you’ve let your IT team know about your suspicions, and once they’ve made sure that no Spyware is installed on your devices (and I do mean all of them – make sure they’ve checked your laptop, desktop, cellphone(s) and tablet), you can then take the next step and update your passwords. Even if your devices come up clean and your IT department can find no sign of Spyware, if you are worried that your accounts might be compromised, resetting your passwords is a good idea.
3. Let Others Know
If you feel like you might have fallen for a trick that led to Spyware being installed on your machine, don’t feel embarrassed. It truly does happen to the best of us. But it’s important to let others know that it has happened. Tell your colleagues to look out for the link that you clicked, or to be on their guard for phishing mails. If you think that your email address was compromised, message those who you’ve been in recent contact with, and let them know to check with you before making any payments or sharing personal details. This will ensure that the attacker’s sphere of influence is minimised, and reduce their potential victim pool.
How Can Solid Systems Help?
Here at Solid Systems, we are committed to helping our clients work securely, minimising and mitigating the Spyware risks that they face, and protecting them from cyberthreats in general. This is why we offer a wide range of cybersecurity services, from email security techniques, to IT audits and data compliance, to advanced threat protection, identity and access management, general IT security and beyond.
But one of the biggest assets in working with us as your Managed IT Services Provider is the training that we offer to you and your teams. It is one thing for us to manage your cybersecurity, and another to ensure that you are protecting yourselves by following best practices, and can recognise when your devices and accounts have become compromised. This added layer of understanding sees businesses protecting themselves as far as possible.
If you are ready to take the next step in securing your business against Spyware and other cybersecurity threats, book a consult or get in touch with us today.
Frequently Asked Questions (FAQs)
It’s an overarching term for a wide range of different threats and viruses all aimed at collecting information without your knowledge, and using it to either extort money from you, your vendors and your clients, or to disrupt your operations. It’s a type of malware, or malicious software, which is designed to go undetected for extended periods of time, allowing it to cause as much damage as possible.
Spyware attackers use a number of different tools to gather information about their victims and infiltrate business systems. Some of these tools and types of Spyware include:
- Keyloggers
- Adware
- Tracking cookies
- Trojans
- Ransomware
- Mobile Spyware
Spyware attackers use a variety of techniques to plant malicious software onto user devices. These can include phishing mails which encourage people to click dodgy links or download infected attachments, taking advantage of software vulnerabilities that either haven’t been patched yet (or whose users haven’t installed updates), and either hacking websites or using pop-up ads to entice users to a malicious website where Spyware can be installed.
Spyware is a risk for any business. But SMEs are particularly being targeted by Spyware and other cyberattacks. This is largely because smaller businesses often believe that they cannot afford sophisticated security software, or because they don’t think that they need it. This makes it easier for attackers to compromise their users and login credentials, and infiltrate their systems.
Spyware is often used as a precursor to a bigger attack. Cyberattackers will infiltrate systems and gather data over an extended period of time without ever being noticed. The more information they gain, the more damage an attack can cause. Once they have as much access as they need, they may conduct a ransomware attack, where they encrypt the data or make it otherwise inaccessible until an extortionate amount of money has been paid, or they may leak the information online for other attackers and competitors to take advantage of.
Because Spyware is designed to go undetected, it can be difficult to tell if you have Spyware installed on your devices. There are a couple of signs that you can look out for – Spyware has a tendency to slow machines down, since it is constantly transferring data to an attacker. And while your anti-virus should pick up on Spyware installations, if it’s out of date, or if the Spyware is new and anti-viruses have not picked up on it yet, there is a chance that it can pass by undetected.
Popular Searches
- Importance of IT Security
- Man in the Middle Attack Prevention
- IoT Cyber Attacks
- Types Of Cyber Attacks
- What is IT Security
- Types of Cyber Security Threats
- Internal IT threats
- What is Cyber Espionage
- How to Prevent Ransomware
- Disaster Recovery Plans
- Cloud vs On Premises
- Types of Cloud Storage
- Sharepoint vs Onedrive